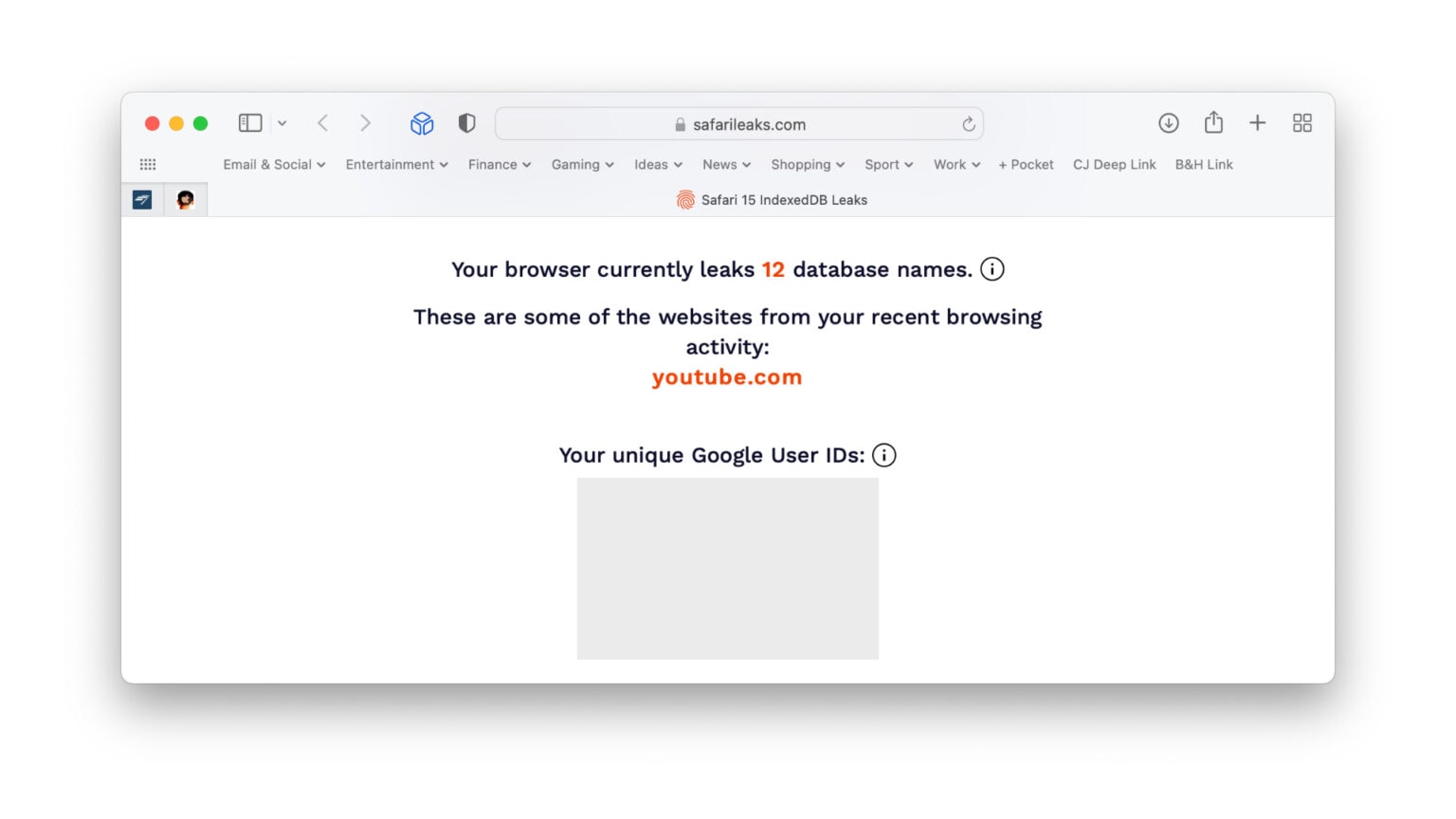
A newly discovered bug in Safari 15 allows any website to track your browsing activity and may even reveal your identity if you’re a Google user.
The vulnerability stems from Apple’s implementation of IndexedDB, a storage API widely supported by most modern browsers. And the problem affects users on Mac as well as iPhone and iPad. Here’s what you need to know.
Safari 15 leaks user data
IndexedDB is a JavaScript API for web browsers that is designed to hold large amounts of data, including files. A wide range of web apps use IndexedDB to store data on your machine to speed things up.
IndexedDB uses what’s called a “same-origin policy” — a security mechanism that restricts how documents or scripts loaded from one origin can interact with resources from other origins. In other words, the same-origin policy prevents one website from accessing data saved by another.
However, in Safari 15, a bug prevents the same-origin policy from working correctly. This gives websites access to the databases created by other sites, allowing them to view your browsing habits outside their walls. What’s more, the bug could even leak your identity.
Beware, Google users
“Moreover, we observed that in some cases, websites use unique user-specific identifiers in database names,” explains FingerprintJS, which first discovered the problem. “This means that authenticated users can be uniquely and precisely identified.”
This is because some popular Google sites — including YouTube, Google Calendar and Google Keep — create databases that include your authenticated Google User ID. This ID is paired with a single Google account (yours), and can be used with Google APIs to fetch user information.
“Note that these leaks do not require any specific user action,” the report warns. “A tab or window that runs in the background and continually queries the IndexedDB API for available databases, can learn what other websites a user visits in real-time.”
Private mode can’t help you
FingerprintJS checked Alexa’s top 1,000 websites to see how many use IndexedDB. It found more than 30 that interact with the API directly on their homepage — without any special user interactions required. So, certain sites could scrape your data and you would know nothing about it.
“We suspect this number to be significantly higher in real-world scenarios as websites can interact with databases on subpages, after specific user actions, or on authenticated parts of the page,” FingerprintJS said.
Sadly, the bug also affects Safari’s Private mode. However, because Private mode restricts browsing sessions to a single tab, it does greatly reduce the amount of information available across multiple sites.
See if Safari bug affects you
You can find out if the Safari bug affects you by visiting FingerprintJS’ proof-of-concept page. With just one click, it shows you what kind of data Safari is leaking about you. It also reveals all the Google User IDs it can detect. It’s just a simple app for demonstration purposes and it’s perfectly safe.
FingerprintJS reported this privacy flaw via the WebKit Bug Tracker on November 28, 2021. There is no fix for it yet. There’s little you can do to protect yourself in Safari 15, either, other than blocking JavaScript entirely. However, this will prevent many websites from working as intended. Plus, it’s not entirely effective.
If you’re concerned about this problem, you’re better off using another web browser until Apple rolls out a fix. And be sure to install any Safari updates as soon as they become available.